Unveiling Proposed CMMC 2.0: Guernsey's Insights and Your Next Move
By: Laura Fawcett, CGEIT, CISM - Guernsey Governance Risk and Compliance Consultant
Key Takeaways and Observations from Guernsey's Initial Review of the CMMC 2.0 Proposed Rule
1. Who will be required to get a certification and at what level? The proposed rule states that the Level of assessment required will be defined in contracts. Estimates were provided as follows:
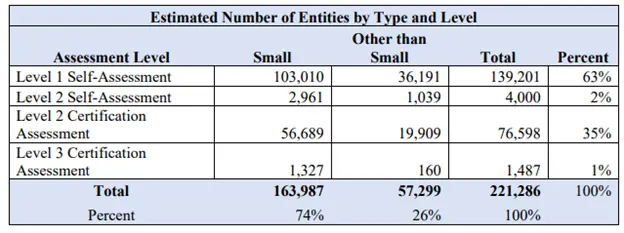
This seems to only speak to numbers for prime contractors and does not include subcontractors. The proposed rule states that if a subcontractor receives FCI and/or CUI as part of the engagement, the applicable assessment level(s) will flow down. As a quick reminder, Level 1 includes the 15 requirements from FAR 52.204-21, Level 2 requires compliance with the 110 security requirements of NIST SP 800-171 revision 2, and Level 3 adds some requirements from NIST SP 800-172 (see details in #3 below) in addition to Level 2.
2. How is CMMC self-assessment different from current self-reporting requirements? CMMC proposed to add an affirmation of conformance when submitting and updating scoring in the Supplier Performance Risk System, known as SPRS. “A senior official from the prime contractor and any applicable subcontractor will be required to annually affirm continuing compliance with the specified security requirements. Affirmations are entered electronically in SPRS."
3. Have level 3 scoping and security requirements been defined? Yes, the proposed rule builds on the scoping for level 2 but does not include the concept of risk-managed assets, and therefore all assets, including Internet of Things (IoT) and Operational Technology (OT) that cannot be verified as out of scope, must be assessed against 800-171 and the applicable (see below) requirements from 800-172.
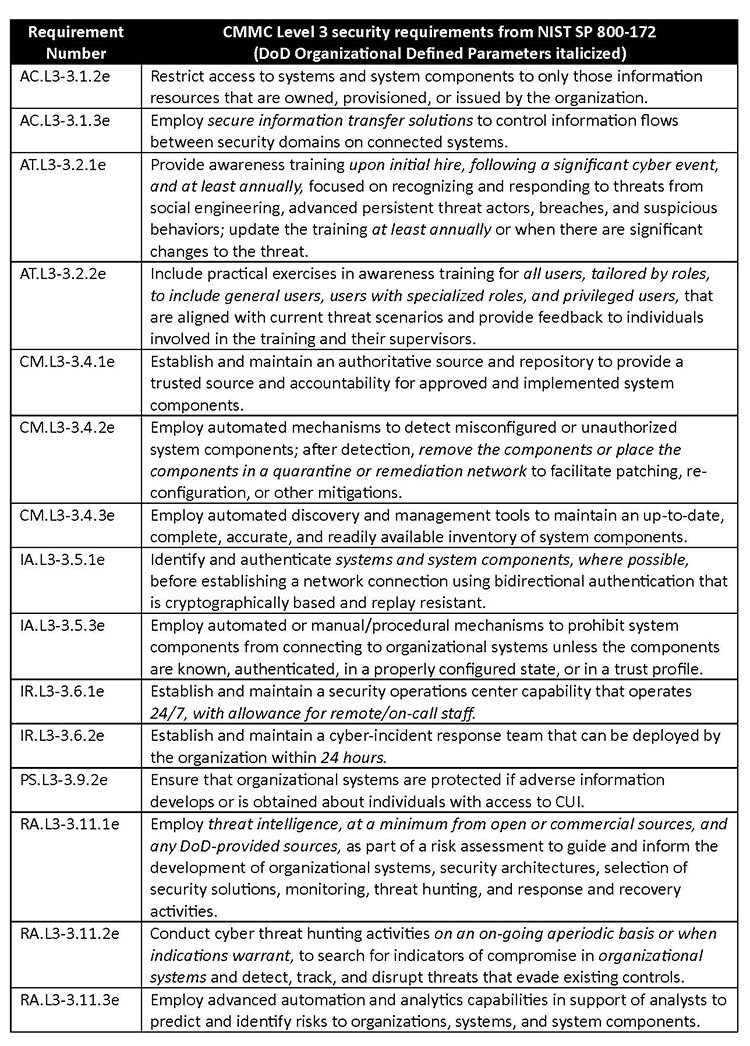
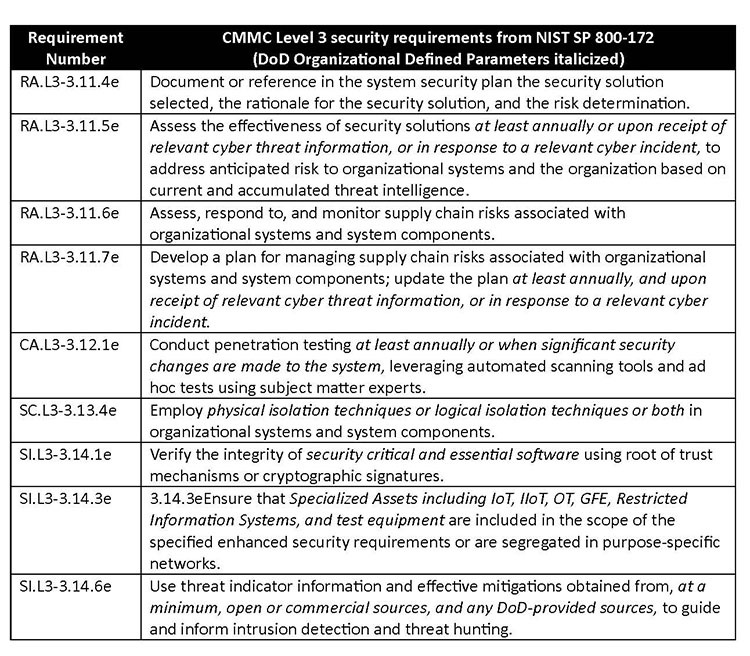
4. Is a perfect 110 score required for certification? The proposed rule allows for Plans of Action and Milestone (POA&Ms) for level 2 self-assessments, certifications, and level 3 certifications when ALL of the following are true:
- The assessment score divided by the total number of applicable security requirements is greater than or equal to 0.8
- None of the security requirements with POA&Ms have a point value greater than 1 (under CMMC Scoring Methodology) except for SC.L2-3.13.11 (CUI Encryption) if it has a value of 1 or 3
- None of the following security requirements have a POA&M:
- AC.L2-3.1.20 (External Connections)
- AC.L2-3.1.22 (Control Public Information)
- PE.L2-3.10.3 (Escort Visitors)
- PE.L2-3.10.4 (Physical Access Logs)
- PE.L2-3.10.5 (Manage Physical Access)
- AC.L2-3.1.20 (External Connections)
5. What about the use of Cloud and External Service Providers? The use of external service providers (ESPs) and Cloud Service Providers (CSPs) has created much debate, especially around how ESPs will be assessed, and how a CSP can achieve “FedRAMP equivalency”. While some definitions were provided, and better guidance about equivalency, we expect a lot of conversation around ESPs. The proposed rule provides the following additional information:
External Service Provider (ESP) means external people, technology, or facilities that an organization utilizes for provision and management of comprehensive IT and/or cybersecurity services on behalf of the organization. In the CMMC Program, CUI or Security Protection Data (e.g., log data, configuration data), must be processed, stored, or transmitted on the ESP assets to be considered an ESP. (CMMC-custom term)
The proposed rule states that “if an External Service Provider (ESP) is used, other than a Cloud Service Provider (CSP), the ESP must have a CMMC Level 2 Final Certification Assessment.” But also states, “If an OSA utilizes an ESP, other than a Cloud Service Provider (CSP), the ESP must have a CMMC certification level equal to or greater than the certification level the OSA is seeking. For example, if an OSA is seeking a CMMC Level 2 Certification Assessment the ESP must have either a CMMC Level 2 Certification Assessment or a CMMC Level 3 Certification Assessment.” One can assume that this means even for a self-assessment the ESP must be Level 2 certified, however, the expected confusion will be around organizations providing consulting or staff augmentation services (often the case with MSPs and MSSPs) related to security that do not ‘process, store, or transmit security logs or configuration data on their owned assets’.
Based on these definitions and the inclusion of cloud solutions as security protection assets, it seems that contractors are expected to only use SIEM, EDR, and Vulnerability cloud solutions that are FedRAMP moderate or equivalent. We expected this might be the case but have serious concerns about how this will impact many contractors. There are few solutions on the market today (and in place at contractors) that meet this high compliance bar.
6. What surprised us the most? We were surprised to see specific reference to NIST SP 800-171 Revision 2 throughout the rule. Revision 3 is already out as a final draft, and it’s likely that Revision 3 may be finalized around the same time or even prior to the CMMC rule finalization. Current DFARs clauses do not specify a specific revision, but once final it can be assumed that those clauses (e.g., 7012) will require compliance with revision 3. It will be very interesting to see how the DoD will handle this and the volume of public comment on this approach.
7. What should you do now? Guernsey’s guidance remains the same, ensure you are complying with current DoD contract obligations. Accurately score yourself against NIST 800-171, document your SSP and POAMs, report your score and POAM dates in SPRS, and work to remediate your POAMs. Keep in mind that once CMMC is finalized you could be required to change some of your security tools (or push those vendors to meet CMMC obligations of 800-171 compliance or FedRAMP equivalency). Don’t forget that the goal is to secure the Defense Industrial Base and protect DoD data and suppliers. Take a risk-based approach to securing your organization: understand your systems, the types of data you have, and how those can best be protected based on threats and vulnerabilities of your organization.
Author: Laura Fawcett, CGEIT, CISM - Guernsey Governance Risk and Compliance Consultant
December 29, 2023

The CMMC Final Rule has been published, and it will be effective on 12/16/2024.
Guernsey is the only Oklahoma based company to have achieved the Certified Third-Party Assessment Organization (C3PAO) status, which authorizes the firm to provide CMMC assessments, or “audits,” for clients seeking certification to meet their contractual obligations.
To schedule your company's C3PAO assessment, contact Timothy Fawcett, CISSP, Vice President Director of Cybersecurity Consulting, at Timothy.fawcett@guernsey.us or (405) 416-8182.



